Bolster your security prospects with real-time protection of critical platforms and apps with 2-Factor Verification.
Allow privileged users to access and manage systems without risk to protected business data. In times of increasing digital crime and online fraud, Fidelity IT Solutions prides itself on safeguarding your business information, keeping out unwanted users and securing access to networks.
With rising threats coming from malicious online sources, it is critical that you have a privileged user access control system in place. We will lay the groundwork for an enterprise-grade two-factor authentication solution that will be integrated into your security architecture to protect your company files and records.
Our comprehensive two-factor authentication will enable an extra, hardened layer of security to the login process, where rights and restrictions are assigned to users. By deploying this advanced security solution, we protect applications, data and users from credential breaches and theft. Our fine-grained, policy-driven two factor authentication solutions drastically reduces incidence of phishing expeditions and identity theft.

Benefits of Two-Factor Authentication
A strong password no longer suffices in a marketplace where business information is highly coveted by malicious parties. It has become commonplace for hackers to unleash a wave of aggressive bots that intend to breakdown and breakthrough your cyber security and steal precious business and personal information.
The 2-factor authentication helps you eliminate concerns that revolve around granting a user access based on a single, knowledge-based factor. Static passwords have led to high-profile breaches, and they can be deciphered. Let our professionals accommodate and handle your switch-over and put you at ease.
The benefits of two-factor authentication solutions provided by Fidelity IT are multifold:
- Simple to use and accommodating, where you leverage something you know (your username and password) with something you have (mobile phones, hardware token etc.)
- Intuitive interface and user-friendly for your staff. No need to train staff.
- Eliminating concerns that your workforce will choose easy-to-guess passwords that can provide an easy pathway into business-critical systems for unauthorized parties.
What is Two-Factor Authentication?
Two-factor authenticity (2FA) is a two-step verification system, where end-users provide two means of identifying themselves to the system. The user, in addition to knowing their username and password, will need to accurately enter a security code, which will be given via text messaging to a user-owned, verified phone number. If a user is unable to provide a security code, they will not be able to gain access.
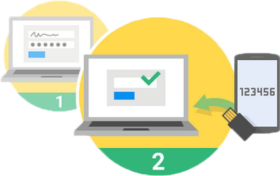
How does Two-Factor Authentication work?
1. Enter your username and password
2. A security code will be sent to your phone, such as a text or voice call
3. You enter the security code that is sent to you to gain access




